MD5 Generator
(No more captcha? Register free!)
How to use this tool?
Introduction:
In the realm of data security, MD5 (Message Digest 5) Generator stands as a reliable tool for generating unique hash values. With its widespread use, understanding how to utilize this powerful tool effectively is essential. In this blog post, we'll take you through a step-by-step guide on how to use the MD5 Generator, providing you with the knowledge to safeguard your data.
Step 1: Accessing the MD5 Generator
To begin, open your preferred web browser and search for an freepiktools MD5 Generator tool. Numerous reliable options are available, and you can choose the one that suits your needs. Once you've found a suitable tool, navigate to its webpage.
Step 2: Inputting the Data
At this stage, you'll encounter a text field where you can enter the data you wish to hash. This data can be a password, a piece of text, or any other information you want to protect. Simply type or paste the desired data into the designated text field.
See the below screenshot:
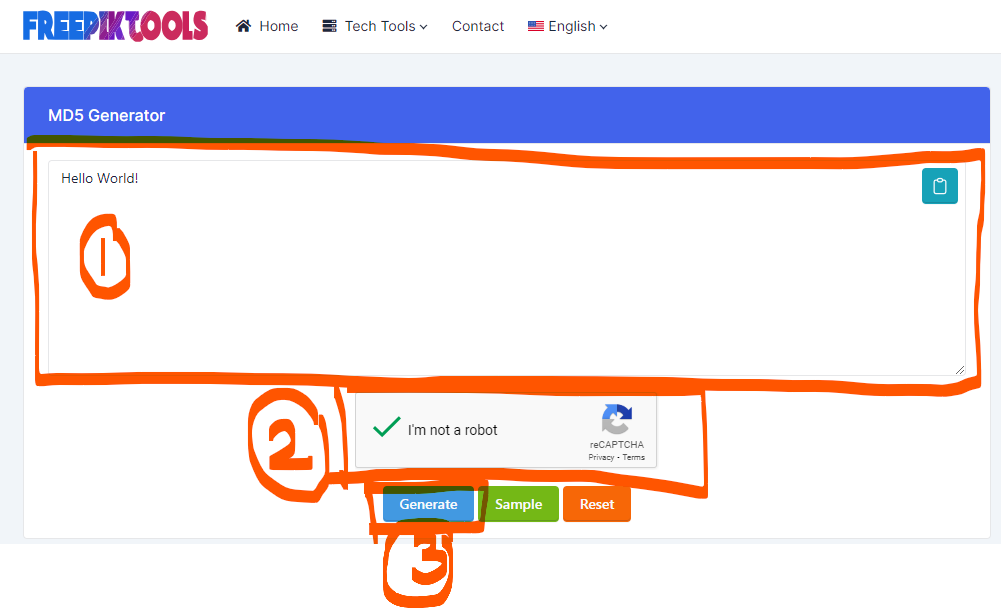
Step 3: Initiating the Hashing Process
After inputting the data, locate the "Generate" button on the MD5 Generator webpage. Clicking this button will initiate the hashing process, where the MD5 algorithm will transform your input into a unique 128-bit hash value.
See the below screenshot:
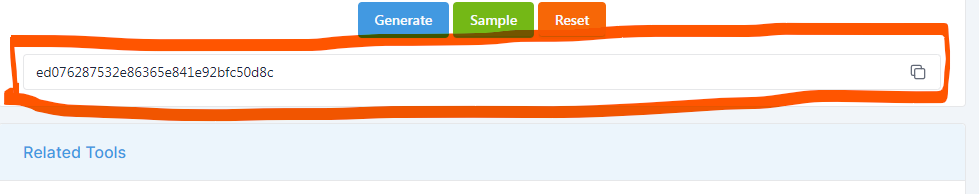
Step 4: Retrieving the MD5 Hash
Once the hashing process is complete, the MD5 Generator will display the generated hash value on the webpage. This hash value is a string of alphanumeric characters and is unique to the input data you provided. You can now copy the MD5 hash to your clipboard for further use.
Step 5: Utilizing the MD5 Hash
With the MD5 hash in your possession, you can employ it for various purposes. One common application is password storage. Instead of storing actual passwords, websites and applications often store the MD5 hashes of passwords. This ensures an additional layer of security, as the original passwords cannot be easily reverse-engineered from the hash values.
Step 6: Verifying Data Integrity
In addition to password storage, MD5 hashes are frequently used for data integrity verification. By comparing the MD5 hash of a file or a piece of data with the original hash, you can quickly determine if any modifications or tampering have occurred. This is particularly useful for verifying the integrity of downloaded files or sensitive data.
Conclusion:
The MD5 Generator is a valuable tool in the realm of data security, providing a convenient and efficient method for generating unique hash values. By following the step-by-step guide outlined in this blog post, you can harness the power of MD5 to safeguard your data, enhance password security, and verify data integrity. Remember to exercise caution and explore other advanced hashing algorithms for more robust security needs.

Dr. Vinod G
Founder of ETSPL / BEPPL / Consult Innservices / Cyber Expert
Welcome to my corner of the digital world, where expertise meets insight, and solutions are crafted with precision. As a seasoned blog writer, cyber expert, and advisory consultant, I am dedicated to empowering individuals and businesses to navigate the complexities of the digital realm confidently. With a wealth of experience and a passion for cybersecurity, I am here to guide you through the ever-evolving landscape of cyber threats and technological advancements.